How to Get Into Cybersecurity (All Experience Levels)

Are you wondering how to break into the cybersecurity field? We can’t blame you — how many jobs out there give you the chance to protect consumers, fight back against cybercrime, and chase down malicious hackers? The elevator pitch for a cybersecurity expert sounds more exciting than a summer action flick!
But cybersecurity doesn’t just provide challenge and intrigue; it also presents an enormous value to the businesses and consumers who need to know that their information will be kept safe from those who attempt to steal and exploit it.
If you ask industry professionals, they’ll give you differing opinions on how to become a cybersecurity expert — that’s because there isn’t one defined educational path that will lead you into the industry. Instead, the route you’ll follow as an aspiring cybersecurity pro will be unique to you, its direction dependent on the experiences you’ve had, the skills you’ve gained, and the roles you hope to hold in the future.
But don’t worry, you don’t have to map out your career path alone! In this article, we’ll walk you through the three most common inroads into cybersecurity:
- How to get into the cybersecurity field if you work in IT
- How to become a cybersecurity expert if you work in another technical field
- How to get into cybersecurity with no experience
We know what you’re thinking: Is it really possible to get into cybersecurity with no experience? The answer is a resounding yes; anyone can build a rewarding career in the industry.
As cybersecurity expert Deborah Hurley told reporters for TechRepublic, “Sometimes it’s perceived that the only way of entering cybersecurity is through the technical door, but that’s not the case. Whatever a person’s talent, with people, administration, management, education, or technology, there is almost certainly an aspect of cybersecurity for which their skills and experience are needed.”
She isn’t exaggerating. As modern life has become increasingly reliant on digital tools, the need for cybersecurity has grown exponentially. In a 2018 Aust Cyber report, researchers estimated that the global cybersecurity market is worth $145 billion and on track to increase 86 percent to $270 billion by 2026.
As you might expect, the increase in market size has led to a similar boost in demand for talent. A recent Cybersecurity Ventures report estimates that there will be 3.5 million unfilled cyber jobs globally by 2021.
Similarly, the Bureau of Labor Statistics estimates that the number of roles for information security analysts will grow 32 percent — more than six times the average for all other professions — between 2018 and 2028. During that time, roughly 35,000 cybersecurity jobs will be added to the American job market alone.
The hiring call isn’t just coming from the tech sector, either; today, nearly every industry is vying for cybersecurity talent. According to a 2019 ISC(2) report, 22 percent of surveyed professionals work in IT, 8 percent in financial services, 7 percent in government, 6 percent in manufacturing, 6 percent in healthcare, 5 percent in education, and 5 percent in retail. The remaining 61 percent is divided into ever-smaller slices across other industries.
For more information about the highest paying cybersecurity jobs, see this guide.
There are clearly many opportunities out there. But how can you best take advantage of them? How can you break into cybersecurity, even if you don’t have the training?
If you’re still curious about exactly how to get into cybersecurity, let’s break it down step by step.
Your entrance into the field of cybersecurity will depend on your work experience. Click one of the following options to jump to a more personalized path based on your professional experience:
- Getting Into Cybersecurity if You Work in IT
- Getting Into Cybersecurity if You Come from Another Technical Field
- Getting Into Cybersecurity if You Have No Technical Experience at All
Getting Into Cybersecurity if You Work in IT
If you have previous experience in IT, you are likely well-oriented to shift gears and start working in cybersecurity. Who knows — you may have already achieved a degree of certification relevant to the field!
Those with previous experience working in IT tend to have hard (and soft!) skills that transition well into cybersecurity. These include but are not limited to:
- Computer science fundamentals
- Programming knowledge
- Creative and technical problem-solving
- Attention to detail
- The ability to communicate about technical subjects in layperson-friendly terms
These skills are so transferable that some IT positions are colloquially known as “feeder roles” for cybersecurity positions. Take networking professionals as an example; according to CyberSeek, professionals who start in network-centric IT roles such as systems administration, network engineering, and solutions architecture often progress into cybersecurity analysis or security engineering roles.
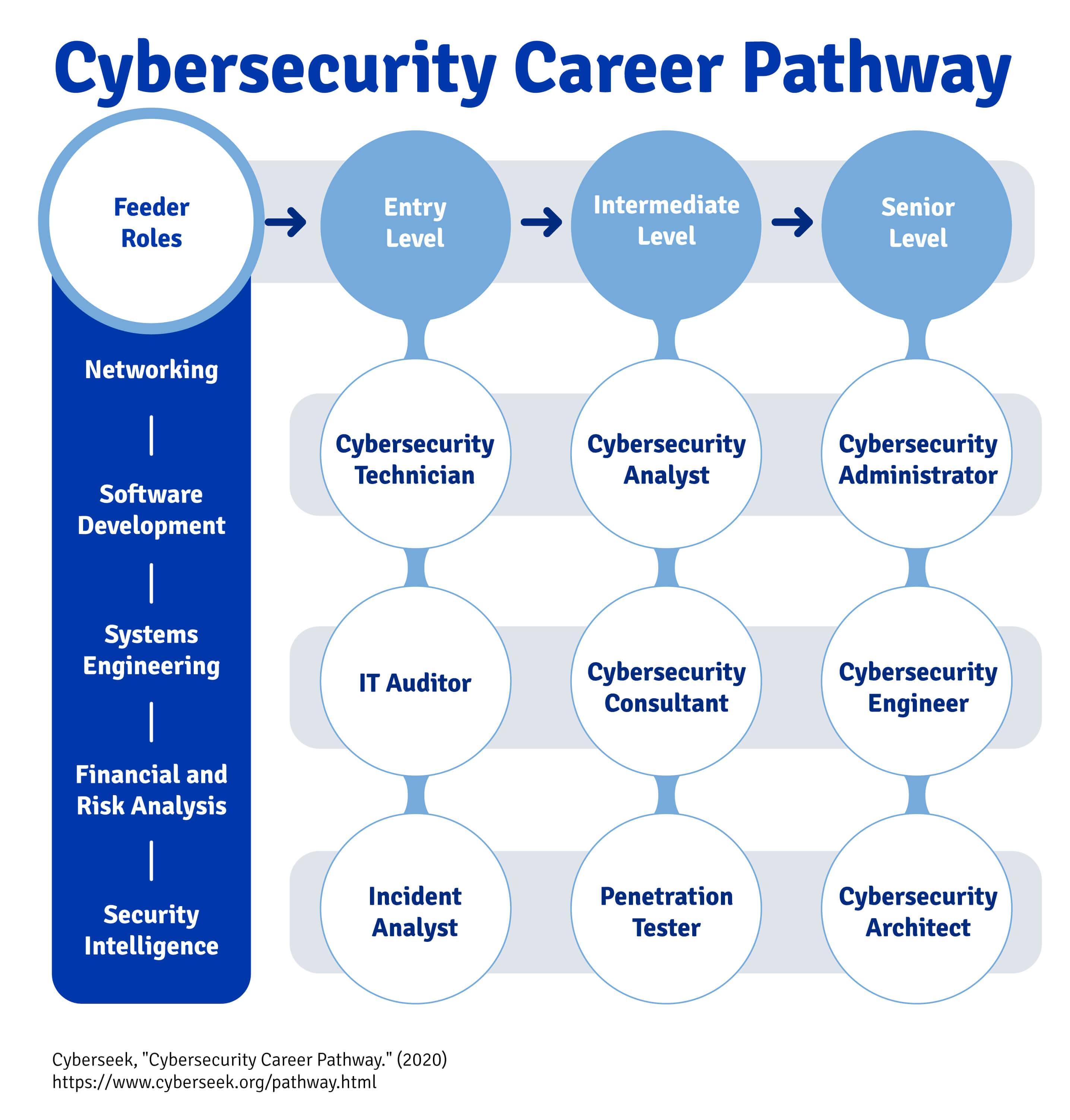
These are just a few roles among many, and many of those with prior experience working in IT can make relatively swift transitions if they so choose. After all, if you have experience in IT and already possess a sturdy foundation of technical skills, you won’t need to re-learn the basics.
That said, the transition won’t be as simple as stepping from one room to another. Even if you work in IT and have prior experience working in tech, you will need to catch up on a few cybersecurity-specific skills.
Technical Skills You’ll Likely Need
Risk Assessment & Management
Risk assessment and management are broad terms that can be applied to both technical and non-technical applications, functions, or processes. When it comes to cybersecurity professionals, it’s all about identifying basic threats, determining risks, and analyzing potential vulnerabilities.
Organizations will likely require you to score systems based on how easily third-party agents could exploit them. There are several threat categories that you may be required to assess. These include but are not limited to gauging the likelihood of data leakage, disruption of service, misuse of information, and malicious unauthorized access.
Cryptography
Cryptography is used to build secure systems that ensure the confidentiality of data, protect against unauthorized access, and authenticate the source of incoming data.
Using cryptography, cybersecurity professionals strive to ensure that sensitive data stays out of the hands of unauthorized agents. Companies rely on professionals to create novel cryptographic algorithms, integrate libraries safely, manage cryptographic keys, and adapt algorithms to keep data securely encrypted.
Security Operations
Security operations refer to broad methods related to preventing, assessing, detecting, monitoring, and responding to ever-changing cybersecurity threats.
Many companies feature dedicated Security Operations teams purely devoted to risk monitoring. To work on such a team, you would need to be able to monitor and identify anomalous activity on networks, servers, databases, or proprietary applications.
Information Assurance
Information assurance is a practice that ensures sensitive data is used, processed, stored, and transmitted in secure ways.
Information assurance requires continual risk assessment and updates to pre-established risk management plans. Cybersecurity teams use this skill to make sure that information is kept confidential, available, and authentic at all times.
Soft Skills You’ll Need
Presentation Skills
Cybersecurity analysts need to communicate effectively with clients and company stakeholders during the risk assessment and management process. You may be called on during meetings to present new findings, such as growing security concerns or anomalous network behavior.
Additional Resources:
- 20 Ways to Improve Your Presentation Skills (WordStream)
- The Biggest Mistakes Made When Presenting Cybersecurity to Senior Leadership or the Board, and How to Fix Them (FireEye)
- 3 Ways to Make a Good Presentation Great (Inc.)
Articulation of Complex Subjects
Above all else, cybersecurity professionals need to be able to communicate clearly about very challenging subjects and concisely deliver risk assessment news to those from non-technical backgrounds.
When security communications aren’t delivered clearly, hackers can still thwart organizations by convincing unsuspecting employers to provide passwords, credentials, or access keys. As a result, part of a cybersecurity expert’s role is to teach the organization about the importance — and proper implementation — of effective security protocols.
Additional Resources:
- How to Explain Complex Ideas (Like Tech) to Those Who Don’t Understand (Lifehacker)
- Best Strategies to Communicate Cybersecurity Risk to the Board (Health IT Security)
- How to Explain Anything to Anyone: 4 Steps to Clearer Communication (TED Ideas)
How to Acquire These Skills and Demonstrate Your Experience
If you already work in IT and have extensive technical experience, you should focus on gathering the proper certifications and refining your current skill set.
Employers frequently rely on certifications to measure a job seeker’s expertise, commitment, and passion for the field. This is especially so in cybersecurity; according to a recent report from Global Knowledge, the number of cybersecurity professionals that hold one or more certifications is rising.
In 2018, the computer security firm Exabeam noted that a full 33 percent of cybersecurity professionals have the Certified Information Systems Security Professional (CISSP) designation, while 23.7 percent have the Certified Ethical Hacker (CEH) certificate and 22.7 percent are CompTIA Security+ certified.
Let’s get some context on what these certifications prove:
- Certified Ethical Hacker (CEH): This certification demonstrates that you can use the same techniques hackers do to identify system vulnerabilities and access points. It’s an intermediate-level certification that certifies competency in covering tracks, reconnaissance, maintaining access, and identifying vulnerabilities.
- Certified Information Systems Security Professional (CISSP): Earning a CISSP certification proves to employers that you know how to design, implement, and manage a best-in-class cybersecurity program.
- CompTIA Security+: This is an entry-level certification, perfect for those with at least two years of experience working with networks. The certificate demonstrates expertise in threat management, cryptography, identity management, and risk mitigation.
If you feel that you already have a strong technical foundation from your previous roles in IT, you may want to focus on picking up one or more of these certifications before you begin applying to jobs.
If your technical expertise is lacking, consider investing in a cybersecurity boot camp. Boot camps are short-term, highly intensive training options that equip you with the industry-ready skills you need to succeed, all within three to six months. Cybersecurity boot camps look great on a resume and demonstrate to employers that you have the necessary skills for the role.
Without additional education or experience from a clearly-transferable prior role, you would likely need to craft a knock-out portfolio to prove you have the skills for the job you’re applying for.
Your resume should be similarly impressive, listing the accomplishments, technical expertise, and certifications you feel are applicable front and center. If you’re seeking a role that requires security clearances, make sure to include these next to your core competencies.
Additional Resources:
- How to Become an Information Security Analyst in 2022 (Columbia Engineering Boot Camps)
- How to Showcase your Skills in an Online Portfolio (Cybrary)
- How to Write a Resume for a Cybersecurity Position (Careers in Government)
- How to Write a Good Cover Letter (Cyber Security Jobs)
Getting Into Cybersecurity if You Come from Another Technical Field
If you have a technical background, you likely have at least some of the relevant skills needed to land a cybersecurity job. That said, you will probably need to pick up a handful of cybersecurity proficiencies before sending out job applications.
Those with prior experience working in software development, for example, already have a wealth of experience working with databases, client-side frameworks, and back end technologies — but often need to brush up on information systems, information assurance, and security operations.
Programmers aren’t uniquely positioned, however. Many technical fields act as gateways for roles in cybersecurity. Data from CyberSeek indicates that professionals working in financial and risk analysis, security intelligence, and systems engineering are all common entry points for those who transfer into the field from other tech-centric industries.
Moreover, findings from a 2018 ISC(2) Cybersecurity Workforce study indicate that only 20 percent of employers view candidates having a “cybersecurity or related undergraduate degree” as being the “most important qualification for employment.” On the whole, employers tended to prioritize the following competencies: knowledge of advanced cybersecurity concepts (47 percent), cybersecurity certifications (43 percent), and strong non-technical skills (39 percent).

Let’s break down the skills you’ll need to pick up in the meantime. (Note that these come in addition to those mentioned in the previous section.)
Technical Skills You’ll Likely Need
Identity and Access Management
This term refers to the way valid users, devices, or processes are identified and given access to an organization’s data. Identity and access management — known more colloquially as authentication — is the primary gateway through which everything and everyone passes in and out of a closed (i.e., secure) system.
Cybersecurity professionals can set up new authentication schemes, identify areas that might allow for a data leak, and adapt existing authentication platforms to new situations.
Linux
Linux is a popular open-source operating system that offers more operating flexibilities and transparency than standard operating systems and, as a result, is used by cybersecurity professionals worldwide.
Most cybersecurity tools are written and designed to run on Linux systems. Cybersecurity professionals use special distributions of Linux for penetration testing, ethical hacking, and vulnerability analysis.
Information Systems
Information systems (IS) is a broad term that refers to how information is collected, processed, stored, and distributed inside and outside of an organization. It is a complementary study of hardware, software, servers, and networks.
Having a clear understanding of information routes is a must for aspiring cybersecurity professionals; a crucial aspect of their role is helping companies adapt their information systems processes and structures to lessen risk.
Soft Skills You’ll Need
Collaboration
Cybersecurity specialists must be able to work in close, collaborative environments. Team sizes often depend on the size and needs of their employers. For instance, a mid-sized enterprise might need a team of several people — network analysts, systems engineers, systems integrators, and more — to work in tandem.
The members of these teams serve as cogs in the overarching team’s machine; if they refuse to function in tandem or let emotions create fission between them, the entire operation clatters to pieces. Don’t become the reason for a breakdown!
Additional Resources:
- Destroying the Myth of Solitary Genius (Goins, Writer Podcast)
- Important Teamwork Skills That Employers Value (The Balance Careers)
- 8 Important Tips for Conflict Resolution (The Business Journals)
Problem-Solving Capabilities
Cybersecurity is an industry that hinges on problem-solving. True, professionals in the field might not spend their days racing from breach to breach, but they do dedicate hours to proactively identifying and resolving security flaws. You could say that those in cybersecurity do problem-solve — they just do so before an issue becomes a problem.
Additional Resources:
- A Beginner’s Guide to Becoming a Better Problem-Solver (IQ Matrix)
- Seven Steps for Effective Problem Solving in the Workplace (Mediate)
- Cybersecurity Requires ‘Insatiable’ Problem-Solving Skills (The Wall Street Journal)
How to Acquire These Skills and Demonstrate Your Experience
If you have some technical experience and training but few cybersecurity-specific skills, your best bet will probably be to attend a cybersecurity boot camp. As mentioned in the previous section, these intensive options offer skills-based training at a reasonable cost and within a few short months. Boot camp attendees also have flexibility; many offer full-time, part-time, virtual, and in-person classes to suit all schedules and learning preferences.
(Want to see what a virtual boot camp could offer you? Check out Columbia Engineering’s Cybersecurity Boot camp here.)
We suggest attending hacking events to network, hone your knowledge, and prove your skills to employers. These multi-day hacking marathons (colloquially known as “hackathons”) allow cybersecurity professionals of all experience levels to leverage their unique talents and prove their abilities in a time-constrained, competitive environment.
Hackathons can serve as a proving ground; by participating in one, newbie or aspiring professionals can demonstrate their skills and prove that they have what it takes to thrive in a cybersecurity role.
Getting Into Cybersecurity if You Have No Technical Experience at All
Contrary to popular opinion, you don’t need to be an experienced tech guru to break into cybersecurity.
Take Shelley Westman, the now-Senior Vice President of Alliances and Field Operations at the cybersecurity company Protegrity, as an example. When Westman began her career, she did so as a lawyer. A few years in, she realized that she wasn’t one for the courtroom — but she was well-suited to the cyber scene.
“It’s a myth in the industry that you have to be technical to be in the field of cyber,” Westman once commented for TechRepublic. “We need people who have deep analytical skills, who can talk to clients, and translate technical speak to business value. It’s an end-to-end business.”
So, yes, it’s absolutely possible for you to get into cybersecurity — but you’ll need to invest in some training! Keep in mind that your journey may take longer than one for a person who previously worked in IT or tech, and that’s entirely okay.
Here are the skills you’ll want to focus on gathering. (Keep in mind that the capabilities listed below should be learned in addition to those mentioned in previous sections.)
Technical Skills You’ll Likely Need
Penetration Testing
A penetration test, or pen test, is a simulated attack performed against a system to check for vulnerabilities. Pen tests can be performed on any number of system types, such as API endpoints, front end interfaces, and back end servers.
After carefully planning a test’s parameters, cybersecurity specialists scan the system to understand how the target is supposed to respond to intrusion before attempting to gain unauthorized access.
Analysts perform pen tests at every entry point into an organization’s sensitive data. These pen testers then strive to maintain access and see what information they can gather, which is later followed by analysis and team debrief.
Digital Forensics
Digital forensics refers to the application of investigative techniques to uncover sources of digital crime and hacking attempts. Digital forensics is used both within companies in the event of a data breach and by legal institutions.
Specialists working in forensics must collect digital evidence, carefully retrieve and examine it through approved extraction methods, attempt to find out who created the data, and then report the results to approved authorities.
Cloud Security
Cloud security refers to the way data, applications, and digital infrastructures are protected within the realm of cloud computing. In simple terms, cloud computing refers to the access and manipulation of data stored on third-party servers rather than local machines.
Many businesses rely on third-party companies to store the bulk of their sensitive data, especially if the company’s workforce itself is geographically dispersed. Cloud security involves implementing robust protections that warn you immediately if suspicious events occur.
Soft Skills You’ll Need
Willingness to Learn
Perhaps the most important trait for a new cybersecurity analyst is an eagerness to learn. You should readily admit existing gaps in your knowledge and be receptive to training opportunities. After all, is there anything worse than a colleague who blusters through their work and then refuses to admit their mistakes?
The only way to improve is to keep an open mind and actively try to recognize and resolve the gaps in your education. Everyone makes mistakes; what matters is how you deal with them.
Additional Resources
- Taking Constructive Criticism Like a Champ (The Muse)
- 17 Ways To Develop a Growth Mindset (Lifehack)
- The 5 Best Strategies for Learning on the Job (Inc.)
Management Skills
Even if you take a job in cybersecurity, you probably won’t spend all your career writing code and running tests from a dark cubicle. If you plan to further your career beyond an entry-level role, you need to be able to manage time, people, projects, and resources.
Capable managers are near-invaluable for all organizations, cybersecurity firms included! Invest in your people skills; you’ll see the career returns.
Additional Resources:
- The Top 10 Management Skills You Need (SHRM)
- 4 Ways to Become a Better Mentor (Business News Daily)
- 20 Powerful Ways That Will Lead Your Team to Greatness (Inc.)
How to Acquire These Skills and Demonstrate Your Experience
Yes, it’s true: Those that lack technical know-how will need to play a game of catch-up. The time and resources you have will largely determine your timeline for entering the job pool.
A bachelor’s degree in a technical field or IT is an excellent option if you have yet to earn your undergraduate degree. You’ll receive a comprehensive education and make critical connections with those already in the field.
Of course, college isn’t cheap. It requires a significant financial investment and several years spent off the job market to receive a degree.
Those who lack time or money may want to consider a boot camp instead. In a cybersecurity boot camp, you’ll leave with all the key competencies required to get an entry-level job right away. However, you won’t get the same comprehensive theoretical background as a college graduate.
If you want to supplement your knowledge beyond the practical skills that a boot camp curriculum would provide, consider putting aside some time for independent study! Delving into books and trade magazines can offer a complementary foundation of theoretical and industry knowledge.
Need a few ideas for where to start? We have you covered.
Best Cybersecurity Books for Beginners
- Cybersecurity for Beginners by Raef Meeuwisse
- The Basics of Hacking and Penetration Testing by Patrick Engebretson
- Social Engineering: The Science of Human Hacking by Christopher Hadnagy
Best Cybersecurity Blogs
- Krebs on Security — An investigative journalism hub dedicated to reporting on cybercrime.
- Zero Day — A news site offering 24/7 coverage of breaking cybersecurity headlines.
- SecurityTrails — A source for cybersecurity news, opinions, lessons, and interviews with top industry experts.
Keep in mind that no matter what educational route you choose, you should receive formal certification to demonstrate that you have the skills necessary to perform well in the industry. Refer to the “Certifications” section under the How to Get Into Cybersecurity If You Work in IT heading for more information.
So, Is It Possible to Break Into Cybersecurity?
In short? Yes!
Regardless of your prior experience, it’s more than possible to break into the field. If you’re looking into how to become a cybersecurity professional, you’re already well on your way. Set time aside to consider your previous experience, prior training, and current situation. Which educational route works best for you?
Only you can decide. We wish you the best of luck on your career journey no matter where it might take you!

 Live Chat
Live Chat