As we store and share more personal data online, we need more experts to protect it. Information security analysts are needed to meet that growing demand, since cyber criminals and hackers constantly threaten our digital world by stealing sensitive information, breaching online security systems, and putting people’s internet presence at risk. These malicious users target individuals and companies, governments, and educational institutions. Information security analysts strive to bring order to this chaos and keep our data safe.
That said, how can you become an information security analyst? In this article, we’ll explore the position in depth by focusing on these five key steps to education and employment:
- Determine your goals for entering information security
- Gain an education
- Become certified
- Determine your ideal career path
- Seek employment
1. Determine Your Goals for Entering Information Security
Upon first consideration, information security may bring to mind certain Hollywood-inspired qualities that lend a tenor of high-stakes peril to its perception as a career — after all, information security analysts help safeguard secrets and classified information from the world’s most notorious hackers.
While all this is technically true, information security analysts must first be experts in digital data and the frameworks that protect it. These professionals are masters of information systems, network security, and project management; they analyze databases, test for security vulnerabilities, and possess strong communication and problem-solving skills.
If you’re considering the field, first ask yourself a few questions: What skills do I have and need to learn to become an information security analyst? What do I want to achieve? Where am I interested in working? Many information security analysts enter the role from another field, such as information technology or network administration. They may have experience managing complex computer systems, working with large IT networks, or developing websites.
Others pursue information security as an entirely new career — drawn by the technical challenges and career possibilities, they choose to study information security through a college program, a cybersecurity bootcamp, or on their own.
Any of these paths can lead to a career in information security, but it’s important to set clear goals and expectations for the future you want to pursue.
2. Gain an Education in Cybersecurity
Even experienced programmers — including those with hacking experience — need some form of education or training to become information security analysts.
A strong educational option is to enroll in a bootcamp, which can offer a concentrated information/cybersecurity curriculum. Courses such as the NYC-based Columbia Engineering Cybersecurity Boot Camp offer intensive study, experience with real-world projects, and instructor support. Bootcamps also provide the independence of a short-term, online course that can fit into a work schedule.
A cybersecurity bootcamp can also equip learners with the necessary skills to begin job hunting in as little as 24 weeks. Participants learn the skills employers are looking for: secure network design, risk management, vulnerability assessment, penetration testing, and more.
Bootcamps also cover important topics such as programming languages, working with data clouds, and ethical hacking. Upon completing the course, learners have the education needed to pursue important career certifications, which we’ll cover next.
Bootcamps can be an effective option for tech professionals looking to make a career change. They can also offer a suitable launchpad for motivated people seeking to grow their skills and earning potential within a short time frame.
Alternatively, a traditional college path is a strong way for aspiring analysts to learn industry skills in a more long-term, fixed format. Independent spirits, on the other hand, can pursue a self-guided education through online tutorials, videos, and manuals — though it can be difficult wading through all the material, finding what is relevant and easy to follow, and exercising personal discipline. However, those pursuing this approach can set their pace, learn what and how they want, and avoid paying tuition.
Get Boot Camp Info
3. Become Certified
Aspiring information security analysts should also be aware of the certifications available in the field. Certifications convey expertise in the field and reflect an analyst’s ability to handle the job’s various demands. Since certifications are plentiful and measure different proficiencies, here are a few to consider pursuing:
- CompTIA Security+: This is among the first certifications that analysts seek. The exam tests baseline topics such as assessing threats, working with different technologies, and troubleshooting. It is considered valuable in government and contracting jobs.
- CompTIA Network+: Cybersecurity analysts must be network experts, so this exam covers the essentials of designing and maintaining functional computer networks, including how to secure them.
- Certified Information Systems Security Professional (CISSP): From (ISC)², a cybersecurity professional organization, this certification covers the design and implementation of a complete cybersecurity program.
- GIAC Information Security Fundamentals (GISF): Global Information Assurance Certification offers a variety of certification programs, including forensics, hacker techniques, and cloud security. The GISF covers disciplines such as cybersecurity terminology, networks, security policies, and cryptography. It is a useful certification for those new to cybersecurity.
- Certified Ethical Hacker (CEH): The EC-Council, an e-commerce organization, offers this certification for those who want to use their hacking schools legally. One aspect of the certification is to establish minimum standards for ethical hacking.
Determine Your Ideal Pathway
Upon completing your education and preparing to get into cybersecurity, take a moment to consider your intended career path. Information security is vital to so many industries: business, government, healthcare, telecommunications, education, and more. If you have interest or related experience in one of these fields, your new information security skills could make you more marketable for a related position.
This also is a good time to start building a professional network. Those with work experience should lean on their current professional connections, highlighting their fresh information security skills and desire for new challenges; one of those contacts could potentially offer insight into a great opportunity.
5. Seek Employment
Information security professionals are required across many industries to develop innovative solutions for protecting networks; your opportunity could come from almost anywhere.
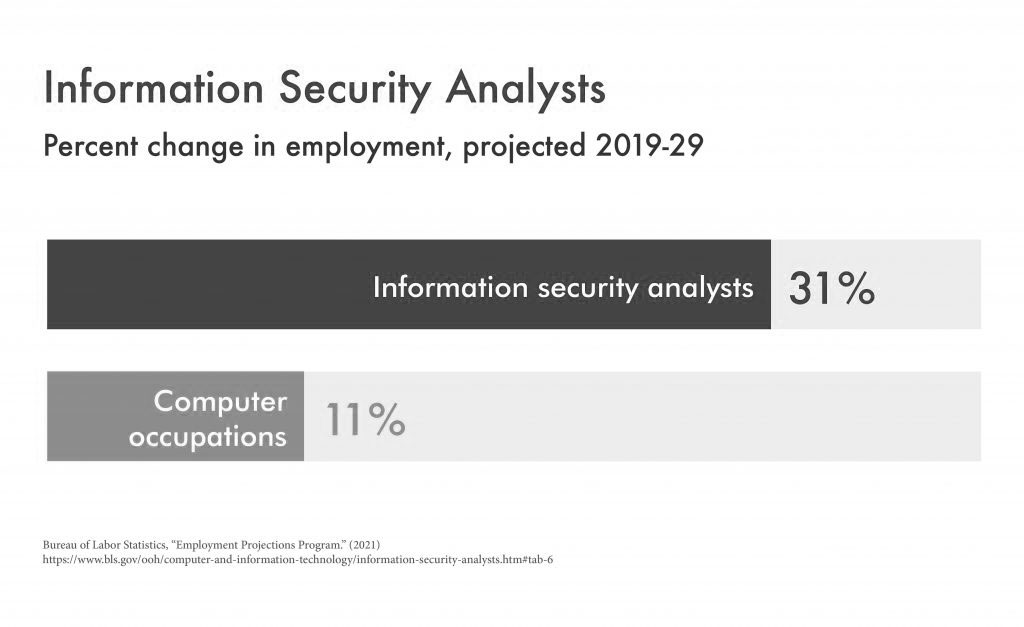
The Bureau of Labor Statistics projects that the need for information security analysts will grow by 31 percent through 2029, far higher than other computer occupations. Further, the need for systems designers, particularly those experienced with cloud computing, will increase by 56 percent.
 Information security jobs are being created almost as quickly as they can be filled, meaning the market is constantly changing. Your professional network might offer interesting job leads — as might online networking sites. LinkedIn, for instance, highlights not only job openings but also professional groups and forums that share ideas, strategies, and, yes, employment opportunities.
Information security jobs are being created almost as quickly as they can be filled, meaning the market is constantly changing. Your professional network might offer interesting job leads — as might online networking sites. LinkedIn, for instance, highlights not only job openings but also professional groups and forums that share ideas, strategies, and, yes, employment opportunities.
On the other hand, online career fairs open access to networking potential across the country, and they serve as a great way to get your name and portfolio out there. To that end, you may also consider launching a personal website that includes your education, work experience, and examples of completed projects (if applicable). Regardless of your approach, remember to be patient with yourself and the job search process.
What Do Information Security Analysts Do? Common Roles and Responsibilities
The information security analyst job description covers a lot of ground, but at its core, the role’s title refers to the act of securing confidential, sensitive, and proprietary information. Analysts protect organizations not only from hacking attempts but also from threats such as phishing, malware, and ransomware. Prevention plays a critical role in information security. Analysts continue to develop stronger and more stable frameworks to protect an organization’s data, and this involves daily analysis for threats and suspicious activity.
Beyond their focus on potential hacking threats, analysts test their own networks to identify vulnerabilities, and they also encrypt sensitive information while developing procedures to maintain an organization’s digital security plan.
Other common responsibilities of information security analysts include:
- Simulating attacks to identify network vulnerabilities (also known as penetration testing)
- Developing and maintaining firewall software
- Monitoring networks and reporting on system breaches
- Instructing employees on how to be safe with their information (passwords, desktop data, confidential information, etc.)
Career Paths in Information Security (and Typically Required Skills)
Analysts think critically to solve problems with integrity and confidentiality. Because of their varied roles, information security analysts have equally varied skills; they’re statisticians, programmers, network administrators, or even hackers — and they may also understand risk assessment and recovery, forensics, and compliance procedures.
Professionals with these skills can theoretically advance quickly through the field; with that in mind, here are a few career paths in information security, ranging from entry to senior level:
Security Specialist
This is an entry-level role that requires a penchant for detailed analysis. Security specialists monitor and maintain an organization’s networks and databases and ensure that corporate and employee data remains safe. Specialists are well-versed in working with information systems and assessing vulnerabilities. From here, specialists can move up to become team leaders and managers.
Incident Analyst
As noted earlier, incident analysts primarily address security breaches. This position requires skill in responding to hacking attempts and preventing them through testing and systems analysis. Key proficiencies include knowledge of systems such as Linux and UNIX and project management experience. Incident analysts also need strong communication skills since they write reports and audits used by managers in non-technical roles.
Information Security Analyst/Consultant
With experience, security specialists can advance to become analysts or consultants. Analysts take on larger roles in a company’s security profile, contributing to the development and installation of a secure framework. Where analysts work for one company, consultants can apply their expertise to multiple companies. Consulting offers information security professionals the opportunity to work for themselves.
Penetration Tester
Penetration testers hack for good by testing an organization’s security by, well, trying to breach it. They also are known as “white-hat hackers” or “ethical hackers” and are especially good at coding, particularly in Python and Java. Penetration testers often have experience as information security specialists, incident analysts, or IT auditors.
Information Security Engineer
This senior role calls for a variety of skills from applying engineering expertise to designing and executing a digital security plan. Engineers oversee a project from its planning stages to its subsequent testing and troubleshooting. The role also requires leadership skills for building a team to develop security policies.
Information Security Architect
Experienced information security analysts are qualified to become architects and lead an organization’s security needs from the ground up. Information security architects design and build security systems, focusing on numerous infrastructural aspects to ensure the system is both fortified and long-lasting.
Salary and Job Outlook for Information Security Analysts
Information security is currently an excellent tech-based career path. We noted earlier that the Bureau of Labor Statistics predicts steady job growth in the U.S. through the 2020s, but that’s just the beginning.
A recent (ISC)² cybersecurity workforce survey noted the global shortage of qualified candidates in the job market. According to the survey, the cybersecurity workforce had more than 4 million unfilled jobs, including 561,000 in North America alone. In order to keep pace with demand, the North American cybersecurity workforce must grow by 62 percent.
The State of New York is a rich market for information security, ranking among the states with the highest salaries, with an annual mean wage of $125,920 and a median salary of $120,660, some of the highest in the country. In particular, the New York-Newark-Jersey City, NY-NJ-PA metropolitan area ranks at the top with an annual mean wage of $130,000.
Generally, those working in information security can expect to be paid well; the median annual salary nationally is $103,590, according to the BLS, with the upper 10 percent of the scale making more than $163,000. Those national numbers are important. Because remote work has made relocating easy, you don’t have to limit yourself to one state or region when pursuing industry work.
See our guide to the Highest Paying Security Jobs.
Why Become an Information Security Analyst?
Whether you’re starting fresh or transitioning from another role, information security offers a new world of professional opportunity — it is fast-paced, constantly changing, and globally relevant. Cyber threats only continue to become more sophisticated by the day, and information security professionals remain our first line of defense.
Ready to get started in this complex, fulfilling career? Columbia Engineering Cybersecurity Boot Camp is a great starting point. Within 24 weeks, you could be on your way to shaping and protecting our digital future.

 Live Chat
Live Chat